Malware type: TrojanThreat sub-type: Spying ToolDestructive: NoPlatform: Android OSEncrypted: NoIn the wild: Yes
|
Low
Medium
|
Infection Channel: Downloaded from the Internet
This malware can be downloaded from fake site that imitates Google Play, formerly known as the Android Market.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.

This Trojan is capable of sending text messages. It first checks the country code and operator code of the affected device. After sending the text message, it then opens a certain site.
This Trojan may be downloaded by other malware/grayware/spyware from remote sites. It may be manually installed by a user.
File size: 2,310,014 bytes
File type: APK
Initial samples received date: 14 Mar 2012
Payload: Sends messages
File type: APK
Initial samples received date: 14 Mar 2012
Payload: Sends messages
Arrival Details
This Trojan may be downloaded by other malware/grayware/spyware from remote sites.
It may be manually installed by a user.
NOTES:
It uses the following icon:

When the application is executed, a user may encounter the following error:

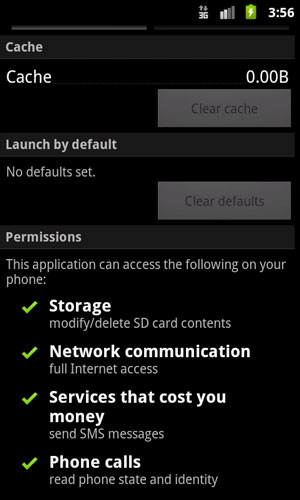
Once installed, this application has the following permissions:

It is capable of sending text messages.
It first checks the country code and operator code of the affected device. If the operator code is 25002, it shows a progress bar with the following text for 6 seconds:
"Click Ok to start sending text message."
Otherwise, it sends the text message directly. The message contains the following text:
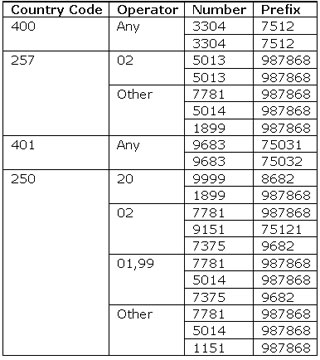
{prefix}+5069+2+p+a
Where {prefix} can be determined by the following table:

After sending the text message, it then opens the following site:
- http://{BLOCKED}oogle.ru/Google_Play.apk




Žádné komentáře:
Okomentovat