Aliases: TrojanSpy:AndroidOS/FakeToken.A (Microsoft); Android.Faketoken (Symantec); Andr/FkToken-A (Sophos)Malware type: SpywareThreat sub-type: Information StealerDestructive: NoPlatform: Android OSEncrypted: NoIn the wild: Yes
|
Low
|
Infection Channel: Downloaded from the Internet
This malware targets mobile banking users by posing as a fake token generator. During execution it asks for the user's password and will generate a fake token while sending the user's information to a specific number and remote servers in the background.
To get a one-glance comprehensive view of the behavior of this Spyware, refer to the Threat Diagram shown below.

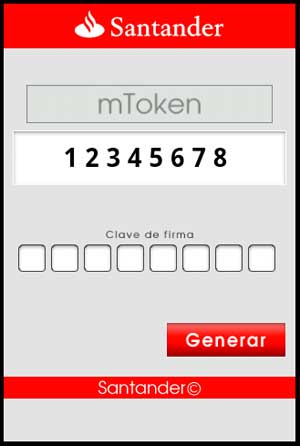
This spyware is an application that poses as a Token Generator from a certain bank. Users must enter a password. Otherwise, it displays an error.
When users click Generar, it generate the fake token and will execute its malicious code in the background.
This spyware may be unknowingly downloaded by a user while visiting malicious websites. It may be manually installed by a user.
File size: 321,292 bytes
File type: DEX
Initial samples received date: 16 Mar 2012
Payload: Displays graphics/image
File type: DEX
Initial samples received date: 16 Mar 2012
Payload: Displays graphics/image
Arrival Details
This spyware may be unknowingly downloaded by a user while visiting malicious websites.
It may be manually installed by a user.
NOTES:
It is an application that poses as a Token Generator from a certain bank. Upon execution, it displays the following:

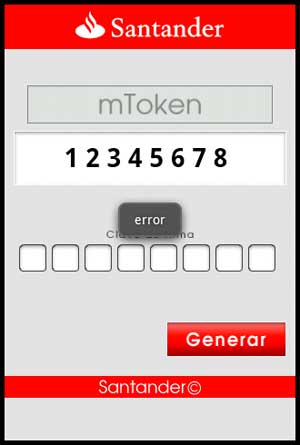
Users must enter a password. Otherwise, it displays an error.

When users click Generar, it generates the fake token and will execute its malicious code in the background. It gathers the following information:
- IMEI
- IMSI
- Phone model
- SDK version
- SID
It sends these information along with the password entered to the following number:
- 79021121067
It also sends these information to the following remote servers:
- http://{BLOCKED}hop.ru/cp/server.php
- http://{BLOCKED}shopbest.com/cp/server.php
It also steals information from the affected device such as:
- Contacts list
- Text messages
It also has the capability to execute itself at a scheduled time. This enables the malware to run a background service and listen for commands from the remote servers. These commands include:
- Update the number where stolen information are sent
- Send the contacts list and SMS messages to the remote server
- Download and install another APK



Žádné komentáře:
Okomentovat